More and more online journalists are using provocative headlines to garner likes and shares while distracting readers from the facts. Bait and switch SEO titles reflect a new trend in yellow journalism, a term first used for nineteenth century United States’ political coverage (published on yellow newspaper) when journalists crafted news to exploit readers’ most vulnerable emotions – fear and curiosity.
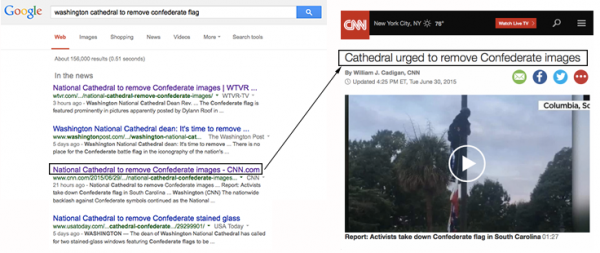
CNN baits readers with an untrue permalink.
The Internet is awash in sensational posts from upstart news sites, but it’s not just the online blogs Upworthy and Buzz Feed doing it. Established news organizations are also using coercive techniques to get clicks.
We’ve busted CNN.com using bait and switch SEO titles to display shocking headlines that are not true.
Consider CNN.com’s recent headlines after Reverend Gary Hall, Dean of the National Cathedral, called on the church’s governing body to remove two stained-glass windows put in place to honor Confederate Generals Stonewall Jackson and Robert E. Lee. His statement immediately (and wrongly) became a mandate, rifling across online social networks courtesy of news organizations that misappropriated the man’s request by writing misleading headlines for their news feeds. Google search results reveal the culprits who use bait and switch SEO titles, particularly where an HTML permalink goes to a story with a different headline than what originally displayed. In this particular example users viewed search results with the title, “National Cathedral to remove Confederate Images – CNN.com” while the destination page displayed the very different headline, “Cathedral urged to remove Confederate images.”
Bait and switch SEO titles allow website managers to differentiate their website posts using what some pundits call “information gaps” in headlines to capture the interests of readers. For example an information gap exists when a headline leaves out details that could have been included: The reason this mom gave for abandoning her baby will surprise you! But the practice of writing sensational headlines becomes misleading when the actual facts are different from the headlines. If, for instance, that article reveals to readers that the mother and baby were penguins, not human beings.
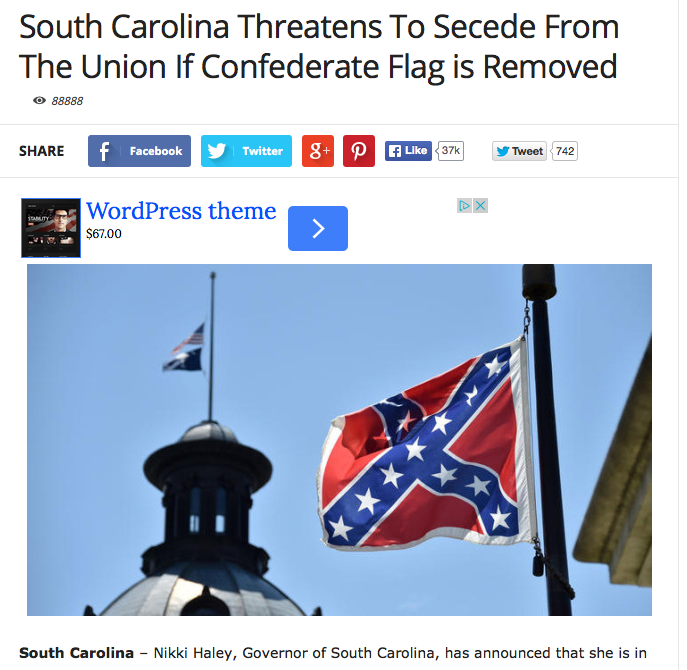
An especially egregious “yellow blog“calling themselves “Newswatch33” has been trolling readers with headlines that South Carolina is actively seceding from the Union, but these yellow journalists take it a step further with the fabrication of facts:
“A petition has been started within the South Carolina House of Representatives for the state to secede from the United States.”
Newswatch33’s false headline is shocking and untrue.
While there is no source sited within the article to support their information, the article carefully embeds that statement between a quote from the Governor and a statement from Leland Summers, the South Carolina Division Commander of Sons of Confederate Veterans who defends the Confederate flag. While it’s true that Summers fails to connect a segregation-era symbol with Charleston’s racist attack, he has not begun a petition to secede nor is there journalistic evidence that any members in the South Carolina General Assembly recently introduced such a petition to secede.
While the prospect of a rogue state makes great headlines, the facts are faked.
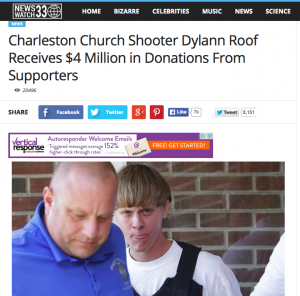
Another bit of their yellow journalism quotes a “Citizen’s for White Rights” source confirming Dylann Roof received $4 million in donations:
“Michael Lawson, attorney for Citizen’s For White Rights released this statement ‘Our organization wants to ensure that Dylann Roof receives fair and equal treatment under the laws of our nation. With all of the publicity this recent incident is receiving along with the Black Organizations looking to make our client guilty, it’s important that Dylann Roof is protected. The donations we are receiving will ensure his protection as we wait for trial as well as when the trial begins.'”
Of course the problem with the article is there is no such person as Michael Lawson, nor a Citizen’s For White Rights organization. The urban legend watch group Snopes.com quickly dispelled the rumor while suggesting the news source “is a fake news site that coincidentally appeared on the scene just after the very similar NewsWatch28 fake news site apparently shut down.”
Perhaps it’s not our fault that we impulsively share these “yellow headlines” without properly vetting them. We want to share our shock with friends! This Information Gap Theory of Curiosity, a phrase coined by George Loewenstein in the early 1990s, explains the psychological phenomenon when readers feel an emotional “itch” on the brain that requires them to scratch it by reading and sharing the headline. That’s the “gap between what we know and what we want to know,” says Loewenstein. Teasing readers by omitting conclusions to a question, displaying images that are purposefully ambiguous, and challenging readers to test sexual, social, moral or morbid assumptions are all tools used to create these unquenchable gaps in headlines.
We have a moral responsibility to ignore agitator websites fanning flames with lies. Those who share bogus bait and switch SEO titles do so to the detriment of relevance. Journalism fails when news is fabricated in this way.
While yellow journalism seems business-as-usual to a few, the misinformation damages critical dialogue by omitting facts that could otherwise enlighten. At worst it causes readers to tune out: “Those folks are far too gone for me to even consider the issues – I just can’t deal with the news anymore!”
We must do better when sharing articles on social media, by vetting the news source and identifying the telltale signs of misleading bait and switch SEO titles meant to elicit more clicks.












 Bait and Switch Website Content
Bait and Switch Website Content