While we’ve got little to gain by revealing how easy it is to get a free Internet phone, here’s hoping the monopolistic phone carriers find an early grave.
There’s little doubt that Google is on target to innovate how we communicate. Rather than forsaking the consumer market who makes phone calls, Google is innovating the way we connect and pay for these phone services. Google Voice calls are free anywhere within North America and costing just a few cents more internationally. But while Google has accommodated the phone lines for these calls, they’ve been remiss in providing hardware to plug into our computers to take advantage of existing hand sets. Speakers and microphones be damned!
Nonetheless, there is new plug-and-play hardware for legacy handsets, hardware that provides the traditional ease and smart ergonomics that (most of us) grew up with. Devices such as MajicJack charge $59.95 up front and yearly fees, but other hardware does better. The Obihai phone adapter, available for $29.99 from NewEgg.com (Use Promo Code: EMCPAWW99) allows direct access to Google Voice and functions the same way AT&T or Verizon land lines work in homes and offices. The only exception – and perhaps one that should be considered – is that 911 calls won’t work. But these devices will offer dedicated E911 VoIP service (for a fee, of course).
5 Steps for How to get an Internet phone for free:
- 1. Purchase Hardware Phone Adapter
- 2. Sign-Up for Google Voice Account
- 3. If calling internationally, add credit to Google Voice
- 4. Plug Hardware Phone Adapter into existing Internet Router
- 5. Use handset to receive and make calls using the Google-assigned phone number
Voicemail, call waiting, caller ID and two-way calls are included in your Google Voice Account. And don’t forget the Visual Voicemail function Google voice is innovating. Now, you don’t have to wade through long pauses while the person on the other end decides what to say on the message. Just read the text:
The OBi device is similar to other adapters which connect to Google Voice.
Obihai is making a marketing push with relentless scorn against phone companies: “With a Google Voice account configured on an OBi device, users will not only get all the great collaboration tools and app integration with Google Voice, they will also be able to enjoy many premium calling features, free calling within the U.S. and Canada and super-low cost international calling – all from the comfort of their home phone,” said Jan Fandrianto, President and CEO of Obihai.
 Calling from a mobile phone doesn’t need to be the default anymore. Sure, an additional piece of hardware has to be purchased and added to your router – but free calls forever on Google Voice is something that we can all celebrate for years to come.
Calling from a mobile phone doesn’t need to be the default anymore. Sure, an additional piece of hardware has to be purchased and added to your router – but free calls forever on Google Voice is something that we can all celebrate for years to come.




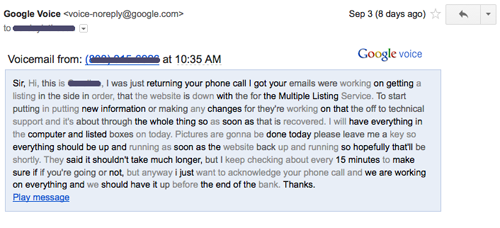

 Contractors and companies bring a charming sales pitch when they promise fast and professional digital media building services, but don’t ignore the vetting process. Choosing a good website builder requires due diligence that ensures they have both technical and marketing prowess. The builder must also have a great support system backing up what they do.
Contractors and companies bring a charming sales pitch when they promise fast and professional digital media building services, but don’t ignore the vetting process. Choosing a good website builder requires due diligence that ensures they have both technical and marketing prowess. The builder must also have a great support system backing up what they do.